FAQ
Frequently Asked Questions
How does RepoGate integrate with our existing SCA tools (like Snyk, Veracode, etc.)?
RepoGate is designed to be a complementary governance and workflow layer that makes the output of your existing Software Composition Analysis (SCA) tools actionable and auditable. We do not replace your SCA tools; we enhance their value. Your SCA tools are excellent at detecting vulnerabilities. RepoGate is the system of record for the decisions you make about those vulnerabilities. When your SCA tool flags a vulnerable package, RepoGate captures the entire lifecycle of that event: the decision to accept the risk, the compensating controls put in place, the approval from the designated authority, and the complete, timestamped audit trail to prove it. This provides a clear, auditable link between vulnerability data and your organization's governance process.
How does RepoGate help with compliance and audits?
RepoGate is purpose-built to solve the challenge of audit and compliance for your software supply chain.
It helps in three key ways:
1. Automated Evidence Collection: RepoGate automatically generates a complete, immutable audit trail for every dependency decision. This eliminates the manual, time-consuming process of gathering spreadsheets, tickets, and emails to prove due diligence to auditors.
2. System of Record: The platform acts as the single source of truth for your dependency governance. When an auditor asks, "Who approved this package and why?" you can provide a definitive, timestamped answer in minutes, not days.
3. Continuous Compliance: By embedding governance policies directly into the developer workflow, RepoGate ensures that your organization is continuously compliant with frameworks like PCI DSS 4.0 (§6.3.2), SOC 2, and ISO 27001, rather than scrambling to prepare right before an audit.
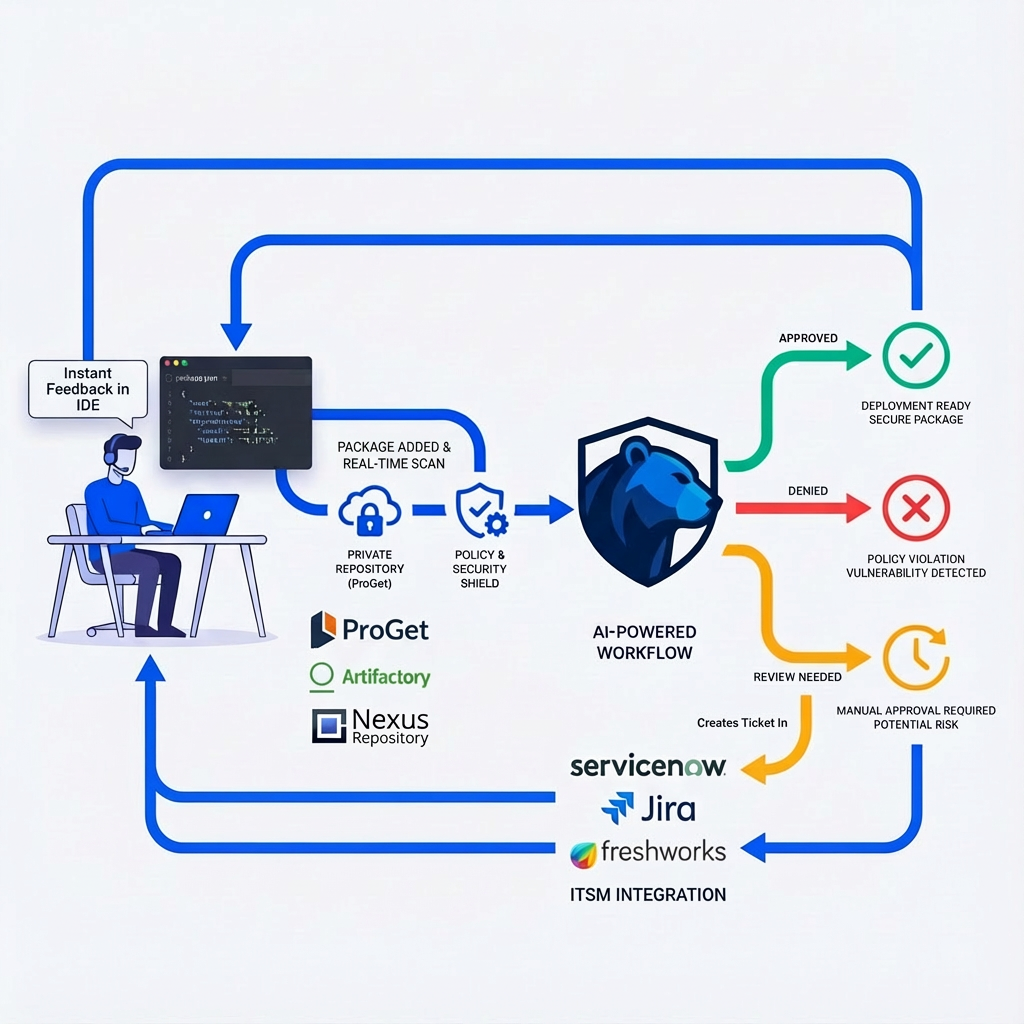
Does every new dependency create a ticket in our ITSM?
No, and this is a key part of our "frictionless governance" philosophy. Tickets are only created when a manual review is explicitly required by your organization's policies. For the vast majority of dependencies that are compliant with your pre-defined rules (e.g., approved licenses, acceptable risk scores), they are automatically approved and logged in the background without creating any tickets or interrupting developer workflow. This ensures that your ITSM is reserved for managing exceptions and high-risk decisions, not flooded with low-value noise.
What is the ROI for our GRC and Security teams?
The ROI is measured in three primary areas:
1. Drastically Reduced Audit Costs: By automating evidence collection, we see customers reduce the time and effort spent on dependency-related audit preparation by over 90%. This translates directly to lower internal costs and reduced billable hours from external auditors.
2. Elimination of Manual Governance Work: Your GRC and security teams can reclaim hundreds of hours per year currently spent manually tracking approvals, chasing down developers for information, and building reports. This allows them to focus on high-value strategic work instead of administrative tasks.
3. Reduced Risk of Audit Findings: A single audit finding can cost tens of thousands of dollars in remediation, fines, and reputational damage. By providing a robust, auditable system of record, RepoGate significantly reduces the risk of costly findings related to your software supply chain.
How do you ensure developer adoption without causing friction?
We ensure adoption by making the path of compliance the path of least resistance.
For developers, the experience is actually faster and more predictable than the alternative.
Instant Feedback: Developers get immediate feedback on dependencies directly in their IDE. They know instantly if a package is approved, denied, or requires review.
Automated Approvals: The majority of dependencies that comply with policy are approved automatically, with no developer intervention required. This is a frictionless experience.
Elimination of Uncertainty: Developers no longer have to guess who to ask for an approval or wait days for a response. The process is clear, automated, and fast, which they appreciate. By removing the manual steps and uncertainty, we create a governance process that developers actually prefer.
What happens if a developer tries to use an unapproved dependency?
The developer receives immediate, real-time feedback directly in their IDE, explaining that the dependency is not compliant with company policy.
Depending on your configured rules, one of two things will happen:
1. Hard Block: The dependency can be blocked from being used entirely.
2. Automated Review Workflow: A formal review process can be automatically initiated in your ITSM (e.g., ServiceNow, Jira), routing the request to the appropriate approvers. The developer is notified that the review process has started. In both cases, the event is logged in the audit trail, providing full visibility to the GRC and security teams.